Our Services
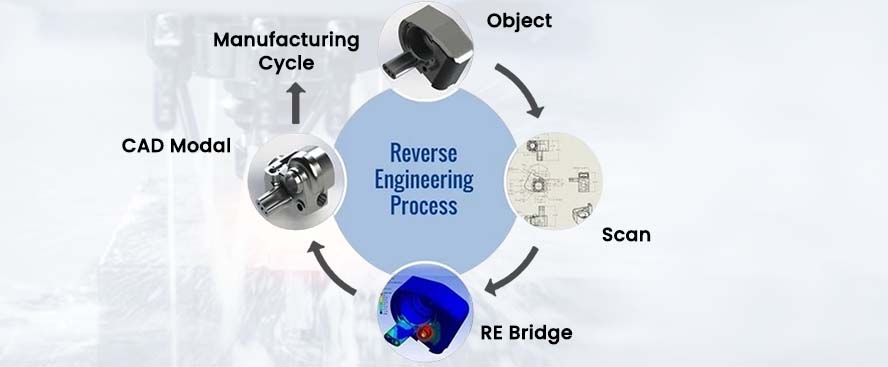
Reverse Engineering
Reverse engineering in the context of a VMC (Virtual Machine Component) typically involves the process of dissecting and analyzing a virtual machine or its associated software components to understand how they work, without access to the original source code or design documentation. This can be done for various purposes, including security analysis, interoperability, and compatibility, or to gain insights into a proprietary or closed-source virtual machine component.
Here are the steps and considerations involved in reverse engineering a VMC component:
- Identify the Target Component: First, you need to identify the specific VMC component you want to reverse engineer. This might be a particular module, function, or data structure within the virtual machine software.
- Reverse Engineering Tools: You’ll need various reverse engineering tools such as disassemblers, debuggers, and decompilers. Tools like IDA Pro, Ghidra, or OllyDbg can be useful. These tools allow you to analyze the binary code of the VMC.
- Code Analysis: Disassemble and analyze the binary code of the VMC component. This process involves converting the machine code into human-readable assembly language and identifying the functionality of different code sections.
- Dynamic Analysis: Run the virtual machine with the target component and use dynamic analysis tools to observe its behavior during runtime. This can help you understand the flow of execution and interactions with other components.
- Documentation and Annotations: As you analyze the code, document your findings and make annotations to help you keep track of the reverse engineering process. This documentation will be invaluable as you work through the component.
- Identify Data Structures: Determine the data structures used by the component, as these play a crucial role in understanding its functioning. You may need to reverse engineer the data structures, which can be a complex task.
- Function Identification: Identify the functions within the VMC component and their purposes. This will help you understand how the component processes data and interacts with other parts of the virtual machine.
- Reconstruction: If the goal is to make modifications or create interoperable components, you may need to reconstruct the code or create proxy functions that mimic the behavior of the original component.
- Testing: Test your reverse-engineered component to ensure that it works as expected and maintains compatibility with the virtual machine or software system.
- Legal and Ethical Considerations: Be aware of the legal and ethical considerations of reverse engineering. Some software licenses and laws may prohibit or restrict reverse engineering activities.
- Documentation and Reporting: Document your findings, techniques, and any challenges you encountered during the reverse engineering process. This documentation can be valuable for future reference and sharing your work with others.
Reverse engineering VMC components can be a challenging task, especially if the virtual machine is complex or the code is heavily obfuscated. It’s important to approach the process with caution, respect copyright and licensing agreements, and consider the implications of your work. Always ensure that you have legal authorization or the appropriate permissions for reverse engineering activities.








